The telecom industry sits at the heart of digital transformation. With 5G deployments, cloud-native architectures, and billions of connected devices, Communication Service Providers (CSPs) are driving the next wave of innovation. However, this progress comes at a cost: an unprecedented surge in cyber threats targeting telecom infrastructure. Traditional security models—designed for static networks—are no longer sufficient.
Enter Security Blueprint: a strategic, automated, and adaptive telecom cybersecurity approach. It is a blueprint for CSPs to anticipate, withstand, and recover from cyberattacks while maintaining business continuity.
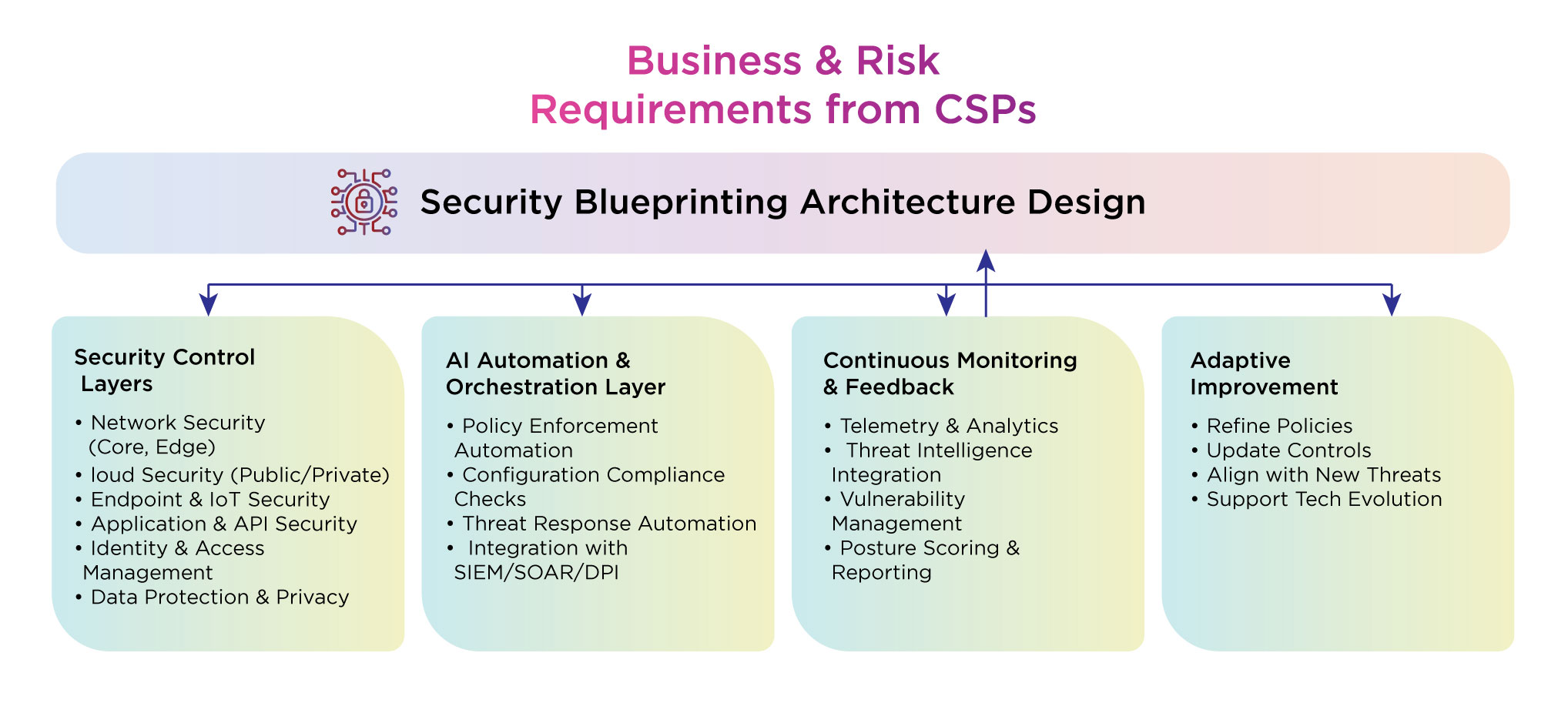
What Is a Security Blueprint?
A Security Blueprint for CSPs is a structured cybersecurity architecture tailored for telecom environments. It combines risk-based design principles, automation, and continuous monitoring to create a resilient security posture. Unlike conventional point solutions, a blueprint provides a holistic view—covering network, cloud, endpoints, and applications—ensuring every layer of the CSP ecosystem is protected.
Think of it as a master plan for telecom security: one that evolves with technology and the threat landscape.
Why CSPs Need a Security Blueprint
Telecom networks are no longer isolated systems—they’re dynamic, distributed, and deeply integrated with IT and cloud environments. This complexity introduces new vulnerabilities:
- 5G and IoT proliferation: Expanding attack surfaces.
- Regulatory pressure: Compliance with stringent telecom security mandates.
- Advanced threat actors: Nation-state attacks and ransomware campaigns targeting critical infrastructure.
- Financial and reputational risk: Downtime or data breaches can cost millions and erode trust.
A Security Blueprint helps CSPs move from reactive defence to proactive resilience, ensuring they stay ahead of evolving threats and meet telecom compliance and security requirements.
Key Capabilities of a Security Blueprint
A Security Blueprint delivers tangible capabilities that strengthen telecom security at every layer:
- Integrated Threat Intelligence
CSPs face highly targeted attacks, including signalling fraud, DDoS on core networks, and supply chain exploits. A Security Blueprint integrates global threat intelligence feeds with local telemetry, enabling CSPs to detect patterns such as anomalous signalling traffic or rogue network elements before they escalate.
Example: Real-time correlation of SS7 or Diameter signalling anomalies with known threat indicators prevents subscriber data leakage. - Zero Trust Architecture for Telecom Networks
Traditional perimeter-based security is obsolete in a 5G and cloud-native world. Zero Trust enforces strict identity verification for every user, device, and workload—whether inside or outside the network. This includes micro-segmentation of network slices and enforcing least-privilege access for orchestration platforms.
Impact: Reduces lateral movement of attackers within virtualised network functions (VNFs) and edge nodes. - Automated Incident Response and Orchestration
Telecom environments generate massive volumes of logs and alerts. Manual triage is impractical. Security Blueprint leverages SOAR (Security Orchestration, Automation, and Response) to automate containment actions—such as isolating compromised network slices or blocking malicious IP ranges—within seconds.
Benefit: Cuts Mean Time to Respond (MTTR) from hours to minutes, ensuring service continuity. - Compliance and Governance Management
CSPs operate under strict regulatory frameworks like GDPR, PCI DSS, CIS standards and telecom-specific standards (GSMA). Security Blueprint includes automated compliance checks and audit-ready reporting, reducing the burden on security teams.
Example: Continuous validation of lawful interception interfaces and encryption standards. - Scalability for Emerging Technologies
With 6G, Open RAN, and edge computing on the horizon, CSPs need security that scales. Security Blueprint supports dynamic policy enforcement across distributed architectures, ensuring consistent protection from the core to the edge.
Benefit: Future-proofing – Enables secure onboarding of IoT devices and edge applications without compromising performance.
Benefits of Security Blueprint for CSPs
Implementing a Security Blueprint delivers strategic and operational advantages:
Enhanced Resilience Against Advanced Threats
CSPs are prime targets for nation-state actors and ransomware gangs. A blueprint approach ensures layered defence, reducing the likelihood of catastrophic outages or subscriber data breaches.
Operational Efficiency and Cost Reduction
Automation and orchestration eliminate repetitive manual tasks, freeing skilled analysts to focus on high-value investigations. This reduces operational expenditure and accelerates incident resolution.
Regulatory Compliance and Risk Mitigation
Non-compliance can result in multi-million-dollar fines and reputational damage. Security Blueprint embeds compliance into daily operations, ensuring CSPs meet evolving telecom security mandates effortlessly.
Improved Customer Trust and Brand Reputation
In a competitive market, trust is currency. Demonstrating robust security measures enhances customer confidence, reduces churn, and positions CSPs as leaders in secure connectivity.
Future-Ready Infrastructure
As networks evolve towards 6G and edge computing, Security Blueprint ensures CSPs can adopt new technologies without introducing security gaps—supporting innovation without compromise.
The Role of Automation in Security Blueprinting
Automation is the cornerstone of modern telecom security. Here is why it matters:
Real-Time Threat Detection and Response. Telecom networks process millions of signalling messages per second. Manual analysis is impossible.
Automation enables AI-driven anomaly detection, flagging suspicious patterns such as SIM swap fraud or rogue base stations instantly.
Predictive Security Through AI and Machine Learning. Beyond reactive measures, automation leverages machine learning to predict potential attack vectors based on historical data and behavioural analytics. (for example, identifying early indicators of DDoS attacks on 5G core before traffic spikes occur).
Workflow Orchestration Across Complex Environments. CSPs operate hybrid infrastructures—physical, virtual, and cloud-native. Automation ensures consistent policy enforcement across these domains, reducing configuration drift and human error.
Compliance at Scale. Automated compliance checks validate encryption standards, lawful interception interfaces, and data privacy controls continuously—eliminating audit surprises and reducing manual overhead.
Incident Containment Without Service Disruption. Automated playbooks can isolate compromised network slices or edge nodes without impacting unaffected services, preserving customer experience during security events.
In essence, automation transforms security from a reactive, labour-intensive process into a proactive, predictive capability—critical for CSPs managing vast, distributed networks.
Building a Resilient Telecom Infrastructure
Creating a resilient telecom infrastructure is not a single deployment—it’s an ongoing transformation that aligns security with business objectives and technological evolution. CSPs must adopt a strategic, layered approach that addresses both current threats and future challenges.
- Adopt a Risk-Based Security Framework
Resilience begins with understanding risk. CSPs should conduct comprehensive risk assessments across their entire ecosystem—core networks, edge nodes, OSS/BSS systems, and cloud-native functions.- Action: Map critical assets and prioritise security controls based on business impact, not just compliance checklists.
- Why it matters: This ensures resources are allocated to protect high-value targets like subscriber databases and signalling systems.
- Embed Zero Trust Principles
Telecom networks are highly distributed, especially with 5G and Open RAN architectures. Implementing Zero Trust ensures that no entity—internal or external—is trusted by default.- Action: Enforce identity verification for every device, API, and workload. Apply micro-segmentation to network slices and edge applications.
- Impact: Prevents lateral movement of attackers within virtualised environments and reduces the blast radius of breaches.
- Integrate Automation and AI Early
Manual security operations cannot keep pace with the scale and complexity of telecom networks. Automation is essential for resilience.- Action: Deploy SOAR platforms to automate incident response workflows, such as isolating compromised VNFs or blocking malicious IP ranges.
- Impact: Reduces Mean Time to Respond (MTTR) from hours to minutes, ensuring service continuity during attacks.
- Build Continuous Monitoring and Threat Intelligence
Resilience is not static—it requires real-time visibility and adaptive policies.- Action: Implement telemetry across signalling protocols (SS7, Diameter, SIP), cloud workloads, and edge nodes. Integrate global threat intelligence feeds to detect emerging attack patterns.
- Impact: Enables proactive defence against telecom-specific threats like signalling fraud, DDoS attacks, and rogue base stations.
- Ensure Compliance and Governance at Scale
Regulatory compliance is a cornerstone of resilience. CSPs must align with frameworks such as GDPR, CIS standards, and GSMA security guidelines.- Action: Automate compliance checks and generate audit-ready reports. Validate lawful interception interfaces and encryption standards continuously.
- Impact: Avoids costly penalties and strengthens trust with regulators and customers.
- Design for Scalability and Future Technologies
Resilience is forward-looking. With 6G, IoT proliferation, and edge computing on the horizon, CSPs need security that scales seamlessly.- Action: Adopt cloud-native security controls and dynamic policy enforcement across distributed architectures.
- Impact: Enables secure onboarding of billions of IoT devices and edge applications without compromising performance.
Bottom Line: Building resilience is a journey that combines risk-based planning, Zero Trust, automation, continuous monitoring, and compliance. CSPs that embrace this holistic approach will not only defend against today’s threats but also position themselves for secure growth in the era of 6G and beyond.
Conclusion
A Security Blueprint provides the strategic foundation to protect telecom networks against today’s threats and tomorrow’s unknowns. By embracing automation, intelligence, and resilience, CSPs can secure their infrastructure while enabling innovation.























![Telco Cloud: A Key Enabler to Telco Transformation [Part 1]](https://www.tatacommunications-ts.com/wp-content/uploads/2023/06/Telco-Cloud-blog_image-1-500x383.png)




