Imagine millions of devices attempting to reconnect after a power outage—only to trigger a silent avalanche of signalling requests that overwhelms your 5G core. No alarms, no explosions—just a creeping flood of retries, loops, and failed procedures that silently degrade service quality. This is the reality of a signalling storm in 5G networks.
As communication service providers (CSPs) transition to cloud-native, service-based architectures, the risk of signalling storms becomes more pronounced. These storms can cripple network functions, disrupt customer experience, and challenge operational resilience.
Understanding Signalling Storms in 5G Core
A signalling storm occurs when an excessive volume of control-plane messages—such as registration attempts, session setups, or authentication retries—floods the network. In 5G Core (5GC), this can overwhelm key network functions like the Access and Mobility Management Function (AMF), Session Management Function (SMF), and Network Repository Function (NRF).
Unlike traditional overloads, signalling storms often originate from misbehaving devices or misconfigured network elements and can propagate across slices and domains due to the distributed nature of 5G architecture.
Causes of Signalling Storms
Signalling storms typically arise from a combination of device behaviour, network misconfigurations, and software anomalies. Key contributors include:
- Faulty UE/IoT Devices: Devices may repeatedly attempt registration or session setup due to firmware bugs or poor retry logic.
- Misconfigured Timers: Inconsistent timer settings across NFs can lead to state mismatches and repeated signalling attempts.
- Software Bugs: Network functions may retry failed procedures too aggressively, causing looping behaviour between AMF, SMF, and UDM.
- Roaming Failures: Incorrect PLMN IDs or missing subscriber profiles can trigger continuous registration retries, especially across V-PLMN and H-PLMN boundaries.
These issues can escalate quickly, especially in dense IoT deployments or during network restarts.
Impact on Network and Customer Experience
Signalling storms degrade both network performance and user experience. Overloaded NFs may drop legitimate requests, delay session setups, or fail to authenticate users. This results in:
- Dropped calls and failed data sessions
- Increased latency and reduced throughput
- Poor QoS and customer dissatisfaction
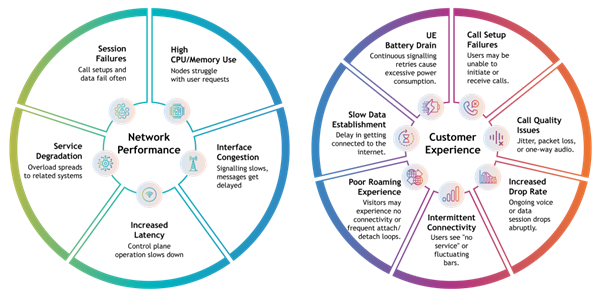
Fig. – Impact of signalling storms on network performance & customer experience
Detection Mechanisms
Effective detection requires a multi-layered approach:
- Core & RAN KPI Monitoring: Track sudden spikes in attach requests, paging load, and authentication failures.
- Per-UE/IMSI Tracking: Identify devices exceeding normal request rates or repeating failed procedures.
- Pattern Analysis: Detect looping message sequences and non-compliance with backoff timers.
- Anomaly Detection via NWDAF: Use AI/ML models to compare live traffic against baselines and flag deviations.
NWDAF in Action
The Network Data Analytics Function (NWDAF) interfaces with AMF, SMF, and other NFs to collect telemetry and apply machine learning models—such as clustering and anomaly scoring—to detect early signs of signalling storms. (Reference: 3GPP TS 23.288)
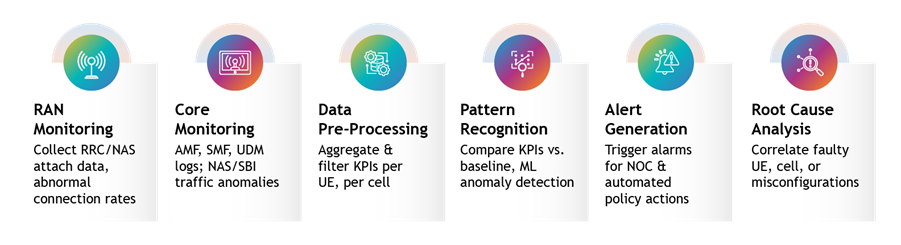
Fig. – Signalling Storm Detection Workflow in 5G Core
Prevention Strategies
CSPs can mitigate signalling storms through proactive and reactive measures:
- Overload Controls & Throttling: Use AMF features like backoff timers and access class barring.
- Limit Device Requests: Enforce retry limits and rate controls.
- Staggered Reconnects: Reconnect devices in batches after outages.
- Device Validation & Updates: Ensure compliance with retry rules and push firmware fixes.
- Temporary Blocking: Isolate problematic regions or device types.
- Robust Network Design: Employ stateless functions, scalable architectures, and redundancy.
- Post-Incident Analysis: Study logs and traces to refine detection and response strategies.
(Reference: 3GPP TS 23.501, TS 29.500)
Signalling storms can breach SLA thresholds for latency, availability, and throughput. Regulatory compliance may be affected, especially in critical services like emergency calling or enterprise connectivity. TCTS helps CSPs maintain SLA integrity through real-time monitoring, automated containment, and post-event analysis.
Conclusion: Building Resilience in the 5G Era
Signalling storms are silent disruptors in 5G networks. By investing in proactive detection, robust architecture, and cross-domain expertise, CSPs can build operational resilience and ensure seamless service delivery. As networks evolve towards 6G, the lessons from today’s storms will shape tomorrow’s defences.
























![Telco Cloud: A Key Enabler to Telco Transformation [Part 1]](https://www.tatacommunications-ts.com/wp-content/uploads/2023/06/Telco-Cloud-blog_image-1-500x383.png)




